| CPC H04L 63/1425 (2013.01) [G06F 21/554 (2013.01); H04L 9/14 (2013.01); H04L 63/0428 (2013.01); H04L 63/1416 (2013.01); H04L 63/1466 (2013.01)] | 20 Claims |
|
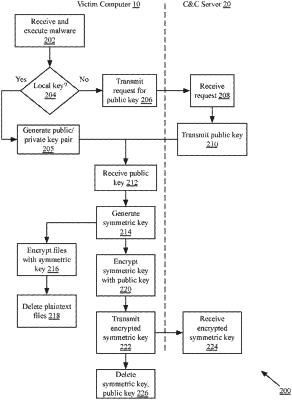
1. A method for detecting and mitigating malicious encryption, comprising:
detecting, by a security agent executed by a computing device, a write operation for a first item of data;
detecting, by the security agent, an encryption key in the first item of data based on the application of one or more tests to the first item of data, wherein the plurality of tests includes:
attempting to decode, by the security agent, the first item of data and analyzing the decoded data for the presence of predetermined strings or formats associated with an encryption key, and
determining if a numeric representation of the first item of data is a composite number and analyzing, by the security agent, the first item of data by attempting at least a partial factorization of the numeric representation; and
responsive to detecting an encryption key in the first item of data based on the application of the one or more tests:
generating an alert, by the security agent, indicating a likely malicious encryption attempt, and
taking, by the security agent, one or more actions to mitigate the malicious encryption attempt.
|