| CPC H04L 63/1416 (2013.01) [G06F 9/451 (2018.02); G06F 16/211 (2019.01); G06F 16/24569 (2019.01); G06F 16/355 (2019.01); G06F 16/95 (2019.01); G06F 21/577 (2013.01); G06F 21/6227 (2013.01); H04L 63/083 (2013.01); H04L 63/102 (2013.01); H04L 63/104 (2013.01); H04L 63/1433 (2013.01); H04L 63/18 (2013.01); H04L 63/205 (2013.01); G06F 2221/034 (2013.01); G06F 2221/2141 (2013.01)] | 18 Claims |
|
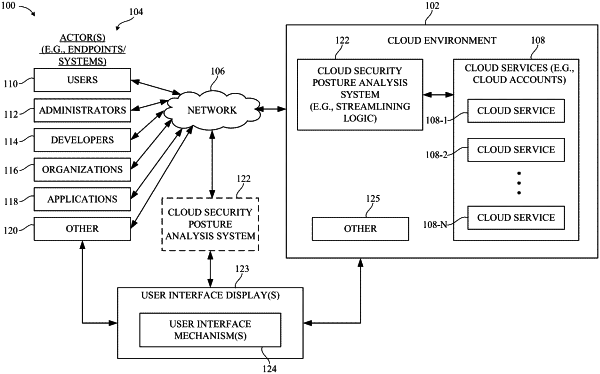
1. A computer-implemented method of streamlined analysis of security posture of a cloud environment, the method comprising:
accessing permissions data and access control data for pairs of compute resources and storage resources in the cloud environment;
tracing network communication paths between the pairs of the compute resources and the storage resources based on the permissions data and the access control data; accessing sensitivity classification data for objects in the storage resources;
receiving a query specifying a subject vulnerability signature; in response to the query, qualifying a subset of the pairs of the compute resources and the storage resources as vulnerable to breach attack based on an evaluation of the subject vulnerability signature relative to the network communication paths and the sensitivity classification data; and
generating a representation of propagation of the breach attack along the network communication paths, the representation identifying relationships between the subset of the pairs of the compute resources and the storage resources,
wherein generating the representation of propagation of the breach attack comprises:
constructing a cloud attack surface map that graphically depicts propagation of the breach attack along the network communication paths as edges between nodes representing the subset of the pairs of the compute resources and the storage resources.
|