| CPC H04L 63/1416 (2013.01) [H04L 63/1425 (2013.01); H04L 63/1458 (2013.01); H04L 63/1466 (2013.01); H04L 65/1104 (2022.05)] | 18 Claims |
|
1. A method, comprising:
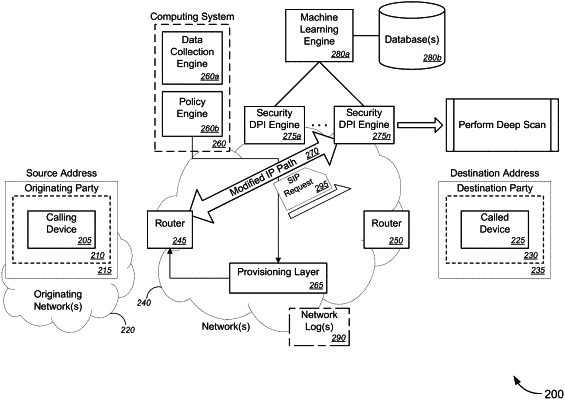
receiving, using a computing system and from a first router among a plurality of routers in a network, first session initiation protocol (“SIP”) data, the first SIP data indicating a request to initiate a SIP-based media communication session between a calling party at a source address in an originating network and a called party at a destination address in the network;
analyzing, using the computing system, the received first SIP data to determine whether the received first SIP data comprises any abnormalities indicative of potential fraudulent or malicious actions;
based on a determination that the received first SIP data comprises at least one abnormality indicative of potential fraudulent or malicious actions, rerouting, using the computing system, the first SIP data to a security deep packet inspection (“DPI”) engine;
performing, using the security DPI engine, a deep scan of the received first SIP data to identify any known fraudulent or malicious attack vectors contained within the received first SIP data and to determine whether the calling party is a known malicious entity or whether the source address is associated with a known malicious entity;
in response to the security DPI engine identifying at least one known fraudulent or malicious attack vector contained within the received first SIP data, initiating one or more mitigation actions; and
normalizing, using the computing system and after initiating the one or more mitigation actions, all network traffic to the destination address after at least one of a predetermined period or a predetermined number of SIP data checks showing no abnormalities indicative of potential fraudulent or malicious actions.
|