| CPC H04L 63/1416 (2013.01) [H04L 63/1425 (2013.01); G05B 19/0428 (2013.01)] | 19 Claims |
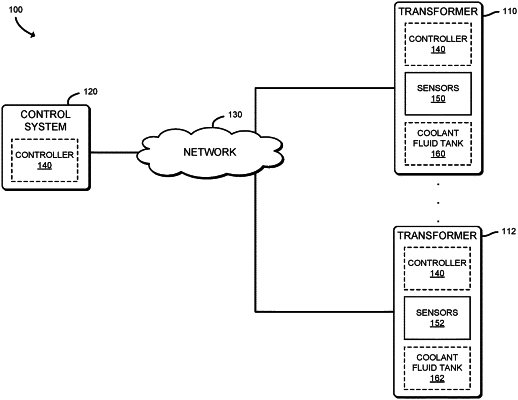
|
1. A method for securing a transformer, the method comprising:
determining, by a controller of the transformer, a plurality of measured values of a first operational parameter of the transformer based upon one or more signals received from one or more sensors of the transformer, the first operational parameter comprising a temperature associated with the transformer, the plurality of measured values comprising a first measured value;
comparing the plurality of measured values to each other;
determining, by the controller based on the comparison, whether the plurality of measured values have stabilized to a predefined load condition;
determining, by the controller, a second measured value of a second operational parameter of the transformer based upon one or more signals received from the one or more sensors of the transformer;
calculating, by the controller, a first expected value of the first operational parameter in response to a determination that that the plurality of measured values have stabilized to the predefined load condition, wherein the calculating is based on the second measured value of the second operational parameter and a model of the transformer that relates the first and second operational parameters;
comparing, by the controller, the first measured value of the first operational parameter to the first expected value of the first operational parameter;
determining, by the controller, a residual value indicative of an effect of noise on a measurement of at least one of the first and second operational parameters of the transformer;
determining, by the controller, whether the residual value is within a predefined upper bound and a predefined lower bound;
identifying, by the controller, that the transformer is subject to a cyber attack when:
a difference between the first measured value and the first expected value exceeds a first threshold, and
the residual value is not within the predefined upper bound and the predefined lower bound;
calculating, by the controller, an expected oil characteristic temperature from at least one of an ambient temperature, an oil temperature from a top of a tank, or an oil temperature from a bottom of the tank;
calculating, by the controller, an expected hot spot characteristic temperature from the at least one of the ambient temperature, the oil temperature from the top of the tank, or the oil temperature from the bottom of the tank;
calculating, by the controller, expected power total loss conditions at the expected hot spot characteristic temperature;
comparing, by the controller, an expected power balance and an expected power total loss;
determining, by the controller, whether the difference between the expected power balance and the expected power total loss exceeds a predetermined threshold; and
executing a corrective action in response to a determination that the difference between the expected power balance and the expected power total loss exceed the predetermined threshold to mitigate an effect of the difference between the expected power balance and the expected power total loss, the corrective action comprising at least one of adjusting a tap changer setting of the transformer and deactivating the transformer in response to the determination that the difference between the expected power balance and the expected power total loss exceed the predetermined threshold.
|