| CPC H04L 63/104 (2013.01) [H04L 63/20 (2013.01)] | 20 Claims |
|
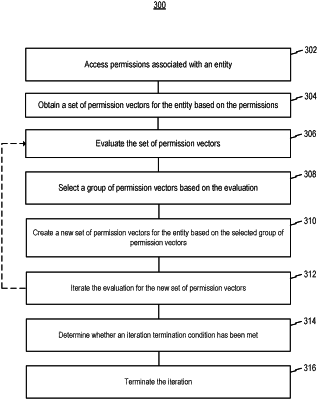
14. A computer-implemented method for iteratively developing least-privilege profiles for network entities, the method comprising:
accessing a set of permissions associated with a network entity;
obtaining a set of permission vectors for the network entity based on the set of permissions;
evaluating each permission vector within the set of permission vectors for iteratively developing a least-privilege profile for the network entity, based on at least:
whether each permission vector within the set of permission vectors provides sufficient privileges for the network entity to perform an action, and
a predefined rule established based on at least one of: a number of permission entries represented by each permission vector, a number of permissions granted by each permission vector, and a similarity of each permission vector to one or more approved permission vectors;
selecting a group of the set of permission vectors based on the evaluation;
creating a new set of permission vectors for the network entity based on at least the selected group of the set of permission vectors;
iterating the evaluation for the new set of permission vectors;
determining, following at least one instance of the iteration, whether an iteration termination condition has been met; and
terminating the iteration based on the iteration termination condition being met.
|