| CPC H04L 63/102 (2013.01) [G06F 9/547 (2013.01); G06F 16/27 (2019.01)] | 18 Claims |
|
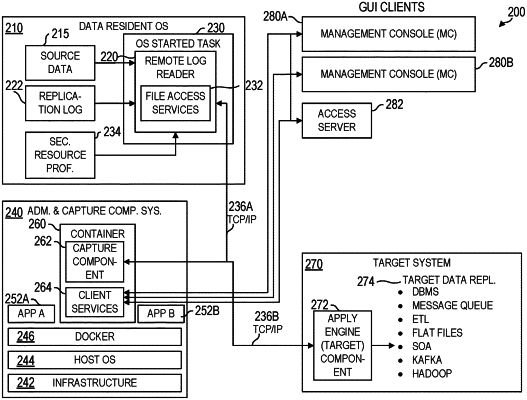
1. A computer implemented method for securing an access of a data object in a datastore by a remote system without user-specific credentials, the method comprising using a processor of a data resident operating system for:
verifying, using a security resource profile for the datastore, which access entity the remote system has access to, but without the user-specific credentials;
providing the security resource profile through a security application program interface (API) to the processor to determine whether access to the access entity should be allowed; and
allowing the access to the data object by the remote system when the security resource profile exists and permits the access;
wherein:
the security resource profile further specifies, for the access entity, a jobname and an Internet Protocol (IP) address that the remote system has access to;
the security resource profile comprises a rule having a specific permission level allowing access to the access entity for the remote system based on the data resident operating system and an administrative and capture components system as one of remote systems being known entities of an access server; and
access to a second access entity is denied in an absence of a second rule related to the second access entity.
|