| CPC H04L 63/061 (2013.01) [H04L 63/0245 (2013.01); H04L 63/029 (2013.01); H04L 63/0435 (2013.01)] | 34 Claims |
|
1. A method for rekeying a security association (SA) in a network system including a first network device and a second network device, comprising:
establishing an Internet Key Exchange (IKE) tunnel and an Internet Protocol Security (IPSec) tunnel between the first network device and the second network device; and
negotiating to rekey a SA by:
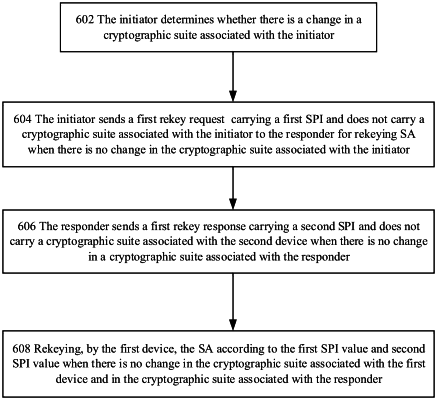
sending, by the first network device, a first rekey request to the second network device for rekeying a SA, wherein the first rekey request carries a first Security Parameter Index (SPI) and a cryptographic suite associated with the first network device;
receiving, by the first network device, a first rekey response from the second network device, wherein the first rekey response carries a second SPI and does not carry a cryptographic suite associated with the second network device when there is no change in a cryptographic suite associated with the second network device; and
wherein:
when the SA is an IPSec SA which is a child SA of an IKE SA, the first rekey request does not carry a Traffic Selector (TS) payload carrying flow information associated with the first network device when there is no change in a flow information associated with the first network device; wherein the first rekey response does not carry a TS payload associated with the second network device when there is no change in a flow information associated with the second network device; and
wherein rekeying, by the first network device, the SA without changing flow information associated with the SA.
|