| CPC H04L 61/4511 (2022.05) [H04L 63/101 (2013.01); H04L 63/126 (2013.01); H04L 63/1483 (2013.01); H04L 2101/69 (2022.05)] | 14 Claims |
|
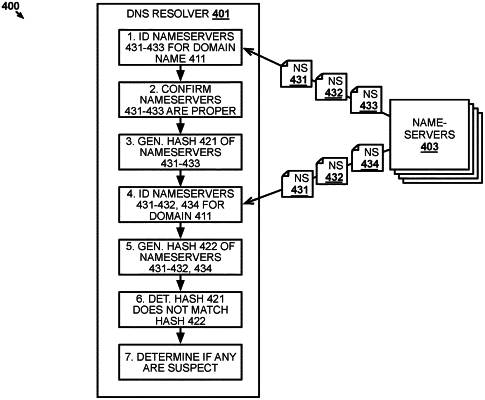
1. A method for operating a Domain Name System (DNS) resolver, comprising:
determining first characteristics of nameservers properly associated with a domain name;
generating a first hash of the nameservers;
generating nameserver criteria associated with the domain name based on the first characteristics, wherein the nameserver criteria defines whether the first characteristics are those of a suspect nameserver for the domain name;
receiving a request to resolve a network address corresponding to the domain name included in the request by a requesting system;
in response to receiving the request:
identifying current nameservers for the domain name;
generating a second hash of the current nameservers;
in response to determining the first hash does not match the second hash,
determining second characteristics of the current nameservers;
determining that at least one of the current nameservers is suspect based on application of the nameserver criteria to the second characteristics; and
preventing the at least one of the current nameservers from being used to resolve the request in response to determining that the at least one of the current nameservers is suspect.
|