| CPC H04L 41/0668 (2013.01) [G06F 16/285 (2019.01); G06F 16/955 (2019.01); G06F 17/18 (2013.01); H04L 12/4633 (2013.01); H04L 12/4641 (2013.01); H04L 41/12 (2013.01); H04L 41/14 (2013.01); H04L 43/04 (2013.01); H04L 43/062 (2013.01); H04L 43/065 (2013.01); H04L 43/0817 (2013.01); H04L 43/0864 (2013.01); H04L 43/0876 (2013.01); H04L 45/02 (2013.01); H04L 45/125 (2013.01); H04L 45/28 (2013.01); H04L 45/302 (2013.01); H04L 45/306 (2013.01); H04L 45/38 (2013.01); H04L 47/125 (2013.01); H04L 47/22 (2013.01); H04L 47/24 (2013.01); H04L 47/32 (2013.01); H04L 47/781 (2013.01); H04L 47/825 (2013.01); H04L 63/061 (2013.01); H04L 67/141 (2013.01); H04L 67/52 (2022.05); H04L 67/63 (2022.05); H04L 69/40 (2013.01); H04L 43/0811 (2013.01); H04L 43/10 (2013.01); H04L 45/22 (2013.01); H04L 61/2503 (2013.01); H04L 61/4511 (2022.05); H04L 61/4523 (2022.05); H04W 84/04 (2013.01)] | 17 Claims |
|
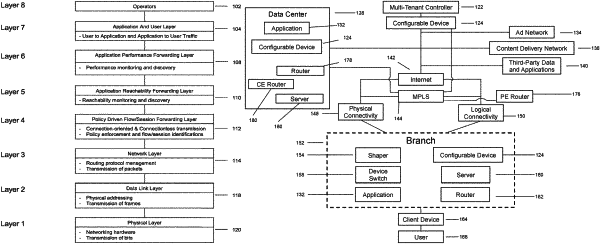
1. A centrally controllable multi-tenant controller for controlling a plurality of assets across a plurality of distributed computing environments wherein the controller is configured to:
receive from a first network tenant on a network:
an indication of a partner network tenant with which to establish a IPSEC VPN TUNNEL, and
at least one of:
a site associated with the partner network tenant to which a IPSEC VPN TUNNEL is to be established,
source prefixes or specific IP addresses at a tenant site from to which application traffic is allowed to travel over the IPSEC VPN TUNNEL, or
destination prefixes or specific IP addresses for application traffic that can travel over the IPSEC VPN TUNNEL;
receive an indication from the partner network tenant of agreement to establish the IPSEC VPN TUNNEL;
instruct one or more devices of the first network and the partner network to establish an IPSEC data tunnel between themselves, wherein only traffic between the source and destination prefixes or specific IP addresses that were specified by the first network tenant and the partner network tenant is allowed to pass through the IPSEC VPN TUNNEL, wherein a most restrictive subset of the source and destination prefixes or specific IP addresses are applied for determining the traffic allowed to pass through the IPSEC VPN TUNNEL, and wherein a policy string defines a business policy based on a first virtual extensible wide area network (VXWAN) network-isolation identifier or a second VXWAN network-isolation identifier; and
determine whether to allow the traffic to pass through the IPSEC VPN TUNNEL based on the policy string.
|