| CPC G06Q 40/12 (2013.12) [G06F 16/27 (2019.01); G06F 16/9035 (2019.01); G06F 21/602 (2013.01); G06F 21/6245 (2013.01); G06Q 10/10 (2013.01); G06F 2221/2101 (2013.01); G06Q 2220/10 (2013.01)] | 33 Claims |
|
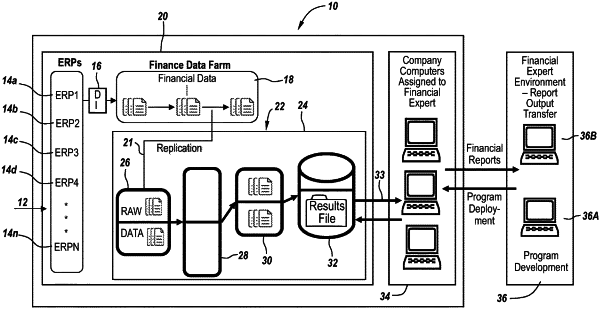
1. A third party data processing system for processing and analyzing financial data of an enterprise, wherein the data processing system is contained and secured within a native environment of the enterprise, comprising
a financial data processing unit of a third party for processing and analyzing the financial data from one or more data sources of the enterprise and located in the native environment of the enterprise, wherein the financial data processing unit comprises a financial data processing unit processor and memory including computer program code, wherein the computer program code of the financial data processing unit, when executed, is configured to cause the financial data processing unit processor to:
receive and store raw financial data from the one or more data sources,
process the raw financial data and generate processed financial data, and
create one or more financial reports from the processed financial data, and
a third party security layer for securing via an encryption technique the financial data processing unit within the native environment of the enterprise so as to restrict access thereto to the third party, thereby preventing access to the processed financial data by the enterprise, wherein the third party security layer comprises a third party security layer processor and memory including computer program code, wherein the computer program code of the third party security layer, when executed, is configured to cause the third party security layer processor to:
filter the raw financial data prior to receipt of the raw financial data,
control access along a communication channel to the financial data processing unit and trace data stored within the financial data processing unit, and
monitor and record connections to the financial data processing unit via the third party security layer, wherein the monitoring and recording of connections is controlled and monitored only by the third party via one or more communication channels, and
an enterprise security layer, wherein the enterprise security layer comprises an enterprise security layer processor and memory including computer program code, wherein the computer program code of the enterprise security layer, when executed, is configured to cause the enterprise security layer processor to secure the financial data of the enterprise and of the one or more data sources such that the financial data processing unit and the third party security layer are secured by the enterprise security layer,
wherein the financial data processing unit and the third party security layer are embedded in the native environment of the enterprise and within the enterprise security layer, wherein the financial data processing unit and the third party security layer are formed from a plurality of dedicated processing nodes separate and distinct from a plurality of nodes of the enterprise, and wherein the financial data processing unit is encapsulated in the third party security layer.
|