| CPC G06Q 20/4016 (2013.01) [G06Q 20/24 (2013.01); G06Q 20/325 (2013.01); G06Q 40/03 (2023.01); H04L 63/101 (2013.01)] | 20 Claims |
|
11. A method, comprising:
receiving, by a device and from a first user device of a plurality of user devices associated with a network, a request to approve a transaction,
wherein a communication session is established between the first user device and a second user device of the plurality of user devices;
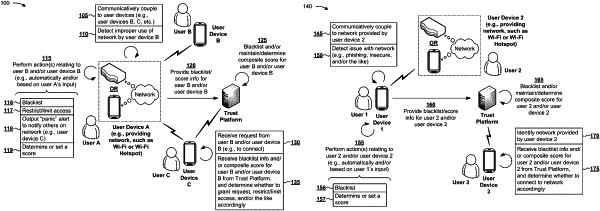
obtaining, by the device and from the first user device and after receiving the request, device identification information associated with the first user device, and data regarding the network,
wherein the device identification information and the data regarding the network are obtained via a trust application configured to detect a network issue,
wherein the trust application is installed on the first user device and the second user device;
wherein network activity of the plurality of user devices is monitored via the trust application, and
wherein inappropriate network activity, associated with the first user device and that includes at least one of hacking, phishing, spamming, or harassing activity on the network, is identified based on monitoring the network activity via the trust application;
receiving, by the device, from the second user device via the trust application, and based on monitoring the network activity, a first score associated with the first user device, and a second score associated with the network, after obtaining the device identification information and the data regarding the network,
wherein the second score is based on one or more scores, provided by the second user device, relating to a level of trustworthiness of the network;
limiting, based on the inappropriate network activity being identified, available bandwidth to the first user device by at least one of:
capping an upload speed associated with the first user device,
capping a download speed associated with the first user device, and/or
capping a total available network data usage associated with the first user device; and
performing, by the device, and based on the at least one of the first score or the second score, an action that includes at least one of approving or rejecting another request to extend credit or the transaction.
|