| CPC G06Q 20/3674 (2013.01) [G06Q 20/0658 (2013.01); G06Q 20/3825 (2013.01); G06Q 20/3827 (2013.01); G06Q 20/425 (2013.01); H04L 9/0637 (2013.01)] | 20 Claims |
|
1. A cryptocurrency securing system, comprising:
a first apparatus, comprising:
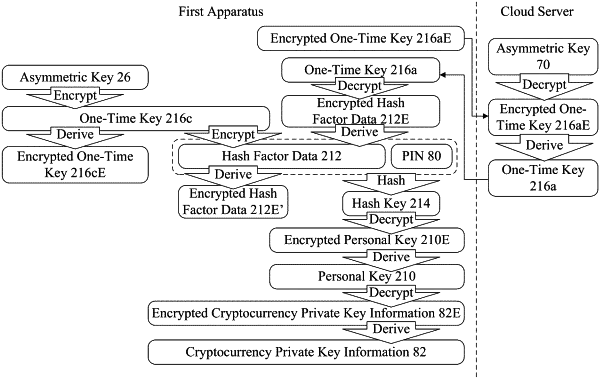
a storage device storing an encrypted one-time key, encrypted cryptocurrency private key information, encrypted personal key, and encrypted hash factor data;
a first network interface; and
a first controller, being configured to:
receive, using the first network interface, a cryptocurrency transaction information from a first user device through a second apparatus;
determine whether policy data corresponding to the cryptocurrency transaction information is compromised;
in response to a determination that the policy data corresponding to the cryptocurrency transaction information has not been compromised:
transmit the encrypted one-time key to a cloud server, wherein the encrypted one-time key is encrypted via an Advance Encryption Standard (AES);
in response to receiving a decrypted version of the encrypted one-time key from the cloud server, decrypt the encrypted hash factor data using the decrypted version of the encrypted one-time key to derive a hash factor data;
decrypt an encrypted personal key with a hash key derived from hashing a personal identification number of the first user device and the hash factor data using a hash function, to derive a personal key, wherein the hash function is a Secure Hash Algorithm (SHA);
decrypt the encrypted cryptocurrency private key information using the personal key to derive a cryptocurrency private key;
encrypt the cryptocurrency transaction information using the cryptocurrency private key; and
transmit, using the first network interface, the encrypted cryptocurrency transaction information to a blockchain network through the second apparatus.
|