| CPC G06F 21/78 (2013.01) [G06F 3/0622 (2013.01); G06F 3/0629 (2013.01); G06F 3/0683 (2013.01); G06F 21/31 (2013.01); G06F 21/602 (2013.01)] | 15 Claims |
|
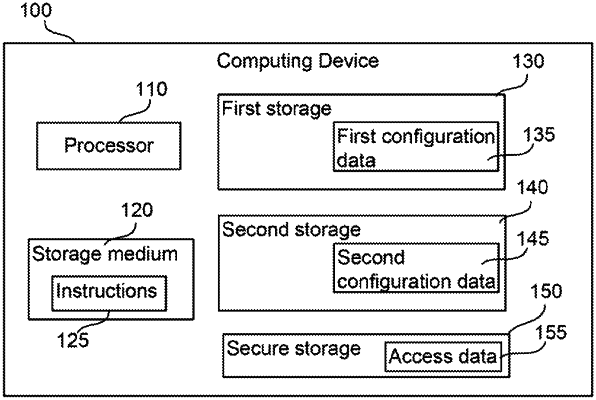
1. A non-transitory computer-readable storage medium storing thereon instructions that, when executed, cause a processor of a computing device to:
read, during start-up of the computing device, first configuration data from a first storage device of the computing device;
read second configuration data from a second storage device of the computing device, wherein the second storage device is not the same as the first storage device, and wherein the second configuration data is a previously made copy of the first configuration data stored on the second storage device;
determine that there is an inconsistency between the first configuration data and the second configuration data;
check a tamper status of the computing device;
clear a secure storage location of the computing device, the secure storage location storing data to access protected data, when the tamper status of the computing device that is checked indicates tampering; and
replace the first configuration data on the first storage device of the computing device based on second data and continue the start-up of the computing device, when the tamper status of the computing device that is checked indicates no tampering.
|