| CPC G06F 21/6263 (2013.01) [G06F 21/6254 (2013.01); G06F 40/205 (2020.01); H04L 63/0428 (2013.01); H04L 63/102 (2013.01); G06F 2221/2119 (2013.01)] | 20 Claims |
|
1. A computer-implemented method for managing privacy policy violations, at least a portion of the method being performed by a computing device comprising at least one processor, the method comprising:
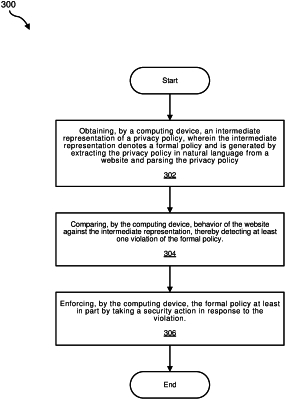
obtaining, by the computing device, an intermediate representation of a privacy policy, wherein the intermediate representation denotes a formal policy and is generated by extracting the privacy policy in natural language from a website and parsing the privacy policy, wherein the extracting includes:
(a) looking for a particular word on the website in one or more languages;
(b) following one or more links associated with the particular word;
(c) downloading one or more documents located at the one or more links;
(d) determining if the one or more documents look like privacy policies; and
(e) recursively following any links found in all of the one or more documents that look like privacy policies;
comparing, by the computing device, behavior of the website against the intermediate representation, thereby detecting at least one violation of the formal policy; and
enforcing, by the computing device, the formal policy at least in part by taking a security action in response to the violation.
|