| CPC G06F 21/6263 (2013.01) [G06F 21/602 (2013.01); H04L 63/105 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
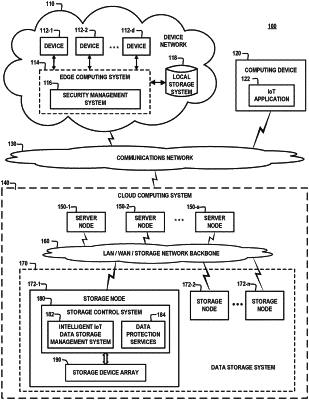
1. A method, comprising:
communicating, by a security management system, with a cloud system to determine different types of data encryption services and secured data analytic services offered by the cloud system;
mapping, by the security management system, a plurality of different data sensitivity levels to respective ones of the data encryption services and the secured data analytic services determined to be offered by the cloud system, wherein the plurality of different data sensitivity levels comprises at least (i) a first sensitivity level, (ii) a second sensitivity level which is greater than the first sensitivity level, and (iii) a non-sensitive level;
receiving, by the security management system, data from a device which operates in a device network that is managed by the security management system;
performing, by the security management system, a data classification process to determine a given data sensitivity level of the received data, wherein the given data sensitivity level comprises one of the plurality of different data sensitivity levels;
determining, by the security management system, at least one of a data encryption service and a secured data analytic service mapped to the determined data sensitivity level of the received data; and
sending, by the security management system, the received data to the cloud system for at least one of (i) storing the data in an encrypted format and (ii) performing secured data analytic processing of the data, utilizing the at least one of the data encryption service and the secured data analytic service mapped to the given data sensitivity level of the received data.
|