| CPC G06F 21/62 (2013.01) [G06F 21/31 (2013.01); G06F 21/604 (2013.01); G06F 21/606 (2013.01); G06F 21/6209 (2013.01); G06F 21/6218 (2013.01); G06F 21/85 (2013.01); H04L 63/0807 (2013.01)] | 20 Claims |
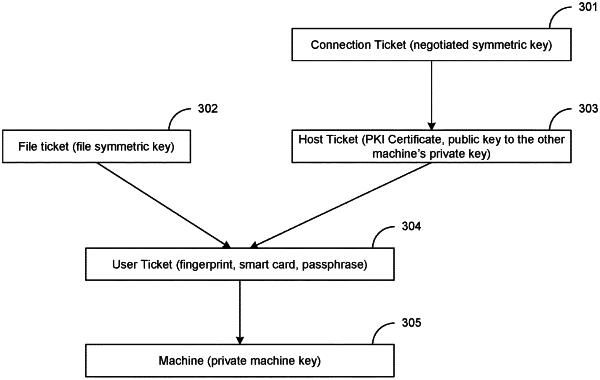
|
1. A method for controlling access to protected content or data, the method comprising:
receiving, at a computer device from a remote user device, a request to access the protected content or data, wherein the request comprises—
credentials associated with the remote user device and a user, the credentials including a user identifier associated with the user of the remote user device and a network resource identifier; and
an indication of an electronic ticket granted to the user, wherein the electronic ticket is separate from the credentials, and wherein the electronic ticket defines access control rules, the access control rules including a time range rule and at least one of a network resource rule or a user identifier rule;
comparing, at the computer device, as defined by the access control rules, the access control rules with (a) a time associated with the received request, and (b) the user identifier from the credentials and/or the network resource identifier from the credentials; and
determining, at the computer device, whether the request to access the protected content or data should be granted based on a result of the comparing,
wherein—
when it is determined that the request should be granted, enabling access to the protected content or data, and
when it is determined that the request should not be granted, denying access to the protected content or data.
|