| CPC G06F 21/604 (2013.01) [G06F 21/32 (2013.01); G06F 21/602 (2013.01); G06F 21/6209 (2013.01); G06F 21/6218 (2013.01); H04L 9/14 (2013.01); H04L 9/321 (2013.01); H04L 63/0861 (2013.01); H04L 63/10 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A method of protecting one or more files, the method comprising:
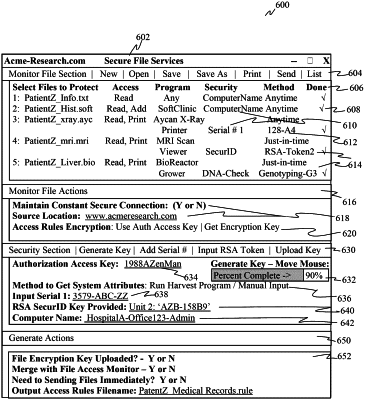
displaying, at an interface of a hardware device, a series of access parameters specifying requirements defining permitted activities relating to the one or more files and encoding specified operational parameters into access rules encoded to be machine readable instructions for a monitor application, the access rules being a set of parameters that are selected at the interface to define permitted activities by the monitor application and an accessing computer system related to the one or more files, the monitor application to control access to the one or more files by the accessing computer system using biometric input to authorize access, the access rules having directions regarding authentication and system attributes that are required to access the one or more files, the access rules providing operational parameters to the accessing computer;
at the accessing computer:
executing the monitor application in the accessing computer system with a computer hardware device;
upon executing the monitor application, continuously running the monitor application on the accessing computer system to control activities of the accessing computer system;
authorizing access to the access rules using the biometric input and confirm rights to access the one or more files;
opening and accessing the one or more files by executing qualifying steps in an authentication process to provide services for the accessing computer system;
successfully authenticating the accessing computer system;
upon successful authentication, controlling activities of the accessing computer system upon the one or more files by the monitor application reading the access rules for a period of active file access of the one or more files by the accessing computer system; and
detecting active file access of the one or more files by the accessing computer system, tracking success and failure of file operations, and supporting the accumulation of logging and tracking data.
|