| CPC G06F 21/602 (2013.01) [G06F 16/172 (2019.01); G06F 21/64 (2013.01); H04L 9/0637 (2013.01); H04L 9/30 (2013.01); H04L 9/50 (2022.05)] | 10 Claims |
|
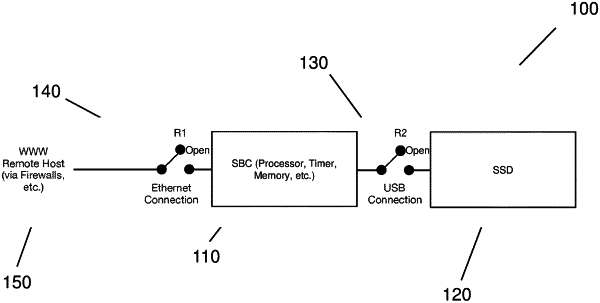
1. A method of securely storing data in a data storage system comprising a data storage device and a security module, said security module initially isolated from the data storage device, and further comprising a remote host, said remote host initially isolated from the security module, said method comprising the steps of:
receiving a data access request to or from the data storage device from the remote host to the security module wherein the security module is connected to the remote host only within a predetermined remote access time window, wherein said remote access time window is stored on the security module, and wherein data access requests from the remote host received outside of the remote access time window in a network based host are queued for later authentication by the security module during the remote access time window;
authenticating the data access request by the security module authenticating the identity of the network based host;
determining whether the data access request is a request to send a file from the remote host to the data storage device or is a request to retrieve a file from the data storage device for sending to the remote host;
where the data access request is a request to send a file from the remote host to the data storage device, receiving the file and caching the file within the security module;
isolating the remote host from the security module;
connecting the security module and the data storage device;
transferring the cached file from the security module to be stored in the data storage device; and
isolating the security module and the data storage device once file transfer is complete.
|