| CPC G06F 21/577 (2013.01) [G06F 21/31 (2013.01); G06F 21/44 (2013.01); G06F 21/45 (2013.01); G06F 21/629 (2013.01); G06F 2221/2113 (2013.01); G06F 2221/2141 (2013.01)] | 14 Claims |
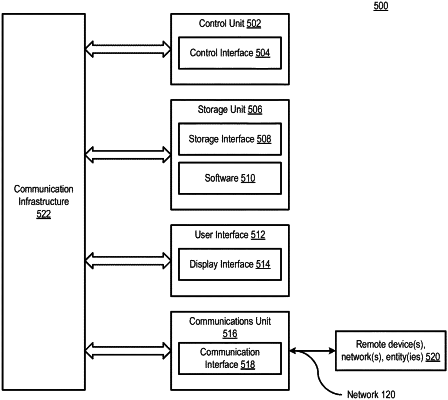
|
1. A computer-implemented method for device fingerprinting, the computer-implemented method comprising:
receiving, at a first time by one or more computing devices and from an application, a first plurality of device attributes identifying a client device on which the application is being used, wherein the first plurality of device attributes comprises first device identification data and a total number of contacts in a first user's contact list;
receiving, at a second time by the one or more computing devices and from the application, an indication that a user is attempting to perform a transaction using the application on the client device;
requesting, by the one or more computing devices and in response to receiving the indication, a second plurality of device attributes identifying the client device on which the application is being used, wherein the second plurality of device attributes is different than the first plurality of device attributes and comprises second device identification data and a total number of contacts in a second user's contact list;
receiving, by the one or more computing devices and in response to requesting the second plurality of device attributes, the second plurality of device attributes;
comparing, by the one or more computing devices, the second plurality of device attributes to the first plurality of device attributes; and
determining, by the one or more computing devices and based on the comparing the second plurality of device attributes to the first plurality of device attributes, a device risk score indicating whether the user is authorized to perform the transaction using the application.
|