| CPC G06F 21/54 (2013.01) [G06F 21/44 (2013.01); G06F 2221/033 (2013.01)] | 24 Claims |
|
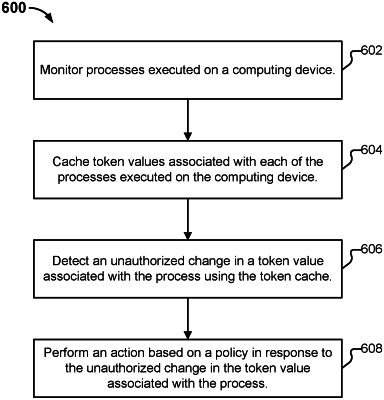
1. A system, comprising:
a processor configured to:
detect an unauthorized change in a cached initial token value associated with a process executed on a computing device, wherein the cached initial token value is checked for changes in response to a trigger event in order to detect an unauthorized change to the initial token value or to detect a stealing of the token by another process executed on the computing device, wherein the initial token value is cached in a data store for caching stored process credentials and tracking processed credential changes, and wherein the data store maintains a cache of processes executing on the computing device along with their credentials and process tree; and
perform an action based on a policy in response to the unauthorized change in the cached initial token value associated with the process to facilitate detection of a token stealing operation after it is completed but before any privileged user mode operation is executed in user mode, wherein the policy comprises a whitelisted set of processes, and wherein the performing of the action comprises to compare the process with one or more processes of the whitelisted set of processes to determine whether to perform the action; and
a memory coupled to the processor and configured to provide the processor with instructions.
|