| CPC G06F 21/32 (2013.01) [G10L 17/18 (2013.01); G10L 17/22 (2013.01)] | 11 Claims |
|
1. A computer implemented method for spoofing proof authentication, comprising:
receiving a signal representing an utterance of a user including a wake up phrase part and a command phrase part;
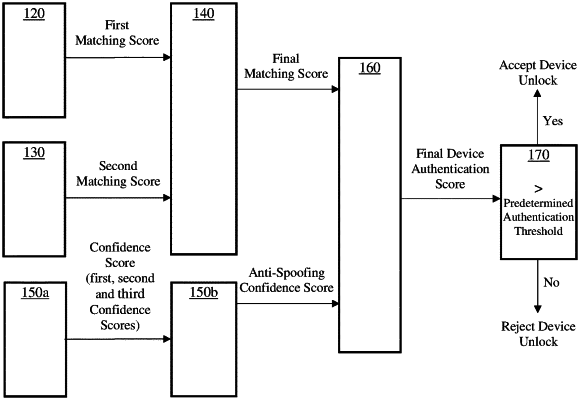
extracting, from the wake up phrase part of the signal, a first set of features and feeding said first set of features to a first pre-trained neural network and matching an obtained result from the first pre-trained neural network with a text-dependent model to assign a first matching score to the wake up phrase part of the signal;
extracting, from the command phrase part of the signal, a second set of features and feeding said second set of features to a second pre-trained neural network and matching an obtained result from the second pre-trained neural network with a text-independent model to assign a second matching score to the command phrase part of the signal;
computing a final matching score of the signal based on the first matching score and the second matching score;
extracting, from the signal including the wake up phrase part and the command phrase part, features and feeding said features to at least one pre-trained neural network to assign at least one confidence score to the signal including the wake up phrase part and the command phrase part;
computing an anti-spoofing confidence score based on the at least one confidence score;
computing a final device authentication score, wherein the final device authentication score is a weighted sum of a log-likelihood representation of the final matching score and a log-likelihood representation of the anti-spoofing confidence score; and
comparing the final device authentication score with a predetermined authentication threshold.
|