| CPC G06F 16/9024 (2019.01) [G06F 18/22 (2023.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); G06N 5/04 (2013.01); G06N 20/00 (2019.01)] | 21 Claims |
|
1. A method for storage-efficient graph pattern matching, comprising:
providing a graph pattern that comprises a set of elements with constraints and connections among them;
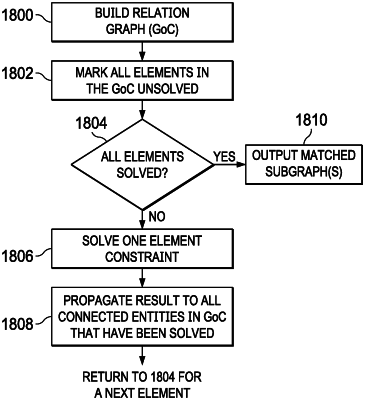
deriving, as a supplemental data structure distinct from the graph pattern, a graph of constraint relations in the graph pattern;
providing an activity graph representing activity data captured in association with one of: a process, a host machine, and a network of machines; and
responsive to a query, finding one or more subgraphs of the activity graph that satisfy the graph pattern by iteratively solving constraints in the graph pattern one at a time, wherein after at least one iteration that solves a constraint is completed and before a next constraint is solved, a result is propagated using a graph traversal of the graph of constraint relations.
|