| CPC G06F 11/1451 (2013.01) [G06N 20/00 (2019.01); G06F 2201/84 (2013.01)] | 4 Claims |
|
1. A data protection method, comprising:
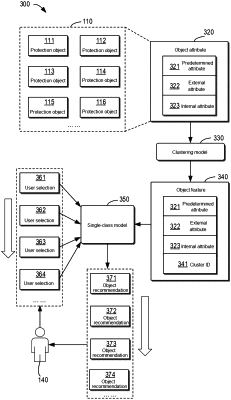
determining an object feature for each protection object in a set of protection objects to obtain determined object features, the set of protection objects comprising a protection object configured with a predetermined data protection strategy, wherein the protection object comprises a predetermined attribute, an external attribute, and an internal attribute, wherein the set of protection objects comprises at least one of the following: a virtual machine, a database, a physical device, or a file system, and wherein the predetermined attribute specifies one of an operating system of the protection object, a size of storage devices of the protection object, and a number of processing units of the protection object;
monitoring the protection object from outside of the operating system of the protection object to obtain the external attribute;
logging into the operating system of the protection object to obtain the internal attribute;
training a classification model based on a corresponding object feature of the protection object, wherein the classification model comprises a support vector machine, wherein the object feature of the protection object comprises a plurality of feature items;
determining, using the classification model, a set of candidate objects belonging to a same class as the protection object according to the determined object feature of the protection object;
ranking the set of candidate objects according to the plurality of feature items to obtain a set of ranked candidate objects;
determining at least one candidate object based on the set of ranked candidate objects; and
configuring the predetermined data protection strategy to include the at least one candidate object.
|