| CPC G01S 7/412 (2013.01) [G06F 18/22 (2023.01); G06Q 50/265 (2013.01)] | 23 Claims |
|
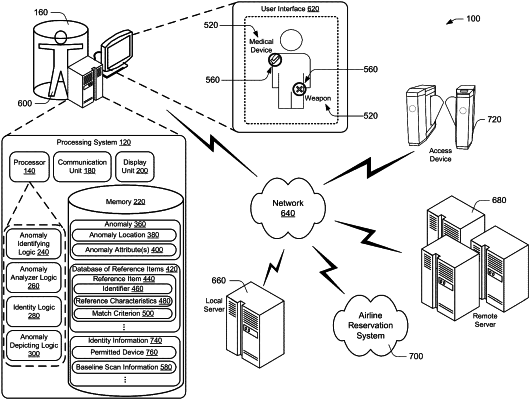
1. A method to obtain identity information and evaluate electromagnetic energy reflection data in view of the identity information, comprising:
determining whether electronic information of a security scan contains an anomaly;
when the electronic information contains an anomaly, identifying an anomaly location in the electronic information corresponding to the anomaly;
determining a subset of the electronic information corresponding to the anomaly location;
determining anomaly attributes using the subset of the electronic information;
evaluating the anomaly attributes using a database of reference items, a given reference item having:
a respective identifier,
respective reference characteristics, and
a respective match criterion indicating one or more of the respective reference characteristics;
making a comparison between the anomaly attributes and the respective reference characteristics of the given reference item;
when a result of the comparison meets the respective match criterion for the given reference item, assigning to the anomaly the respective identifier as an anomaly identifier;
determining an identity of a subject of the security scan;
communicating, by a processing system via a network connection, with a database of a remote server containing stored personal information, to access identity information pertaining to the identity of the subject;
wherein the identity information includes information about the subject that had been provided by the subject and stored in the database in advance prior to the subject undergoing scanning;
determining that the identity information indicates a permitted device for that subject;
determining whether the anomaly is consistent with the permitted device for that subject; and
when the anomaly is consistent with the permitted device for that subject, assigning to the anomaly a pass status.
|