| CPC H04W 12/06 (2013.01) [G06F 21/35 (2013.01); G06F 21/40 (2013.01); H04L 63/061 (2013.01); H04L 63/0853 (2013.01); H04L 63/10 (2013.01); H04W 12/04 (2013.01); H04W 4/80 (2018.02); H04W 12/63 (2021.01)] | 24 Claims |
|
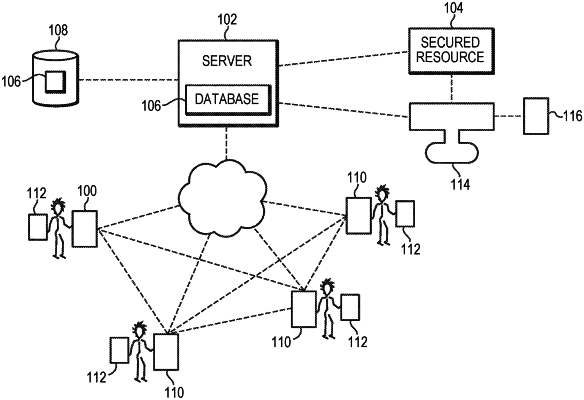
1. A wireless mobile device for accessing a resource to which access is controlled in accordance with a predefined, electronically stored quorum-based authentication policy, the device comprising:
communication circuitry for wirelessly interacting with other mobile devices;
an electronically stored identifier for identifying the mobile device and/or a user associated with the mobile device;
a processor;
a memory; and
an electronically stored application for, upon electronic interaction with one or more other mobile devices, (i) receiving a partial key from at least one of the other mobile devices, wherein the partial key comprises keys contributed by one or more of the other mobile devices, (ii) contributing a key for combination with the partial key into a final key, (iii) receiving a second authentication factor, different from the key, from the user associated with the mobile device, and (iv) transmitting the final key and the second authentication factor to an authentication server,
wherein the resource is accessible to the mobile device only if a combination of the second authentication factor and the final key satisfies the authentication policy.
|