| CPC H04L 63/1441 (2013.01) [G06N 20/00 (2019.01); H04L 41/0686 (2013.01); H04L 47/2441 (2013.01); H04L 63/0428 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/145 (2013.01); H04L 63/168 (2013.01); G06N 20/20 (2019.01)] | 20 Claims |
|
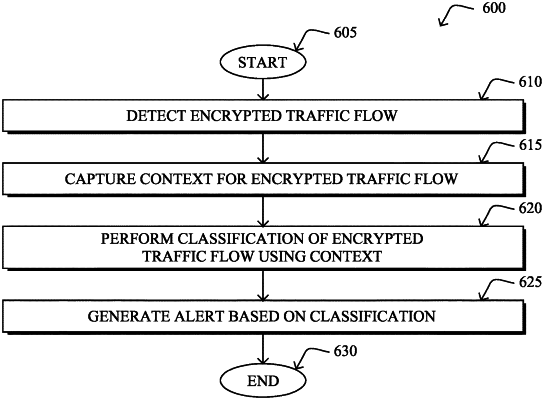
1. A method, comprising:
detecting, at a device in a network, an encrypted traffic flow comprising one or more encrypted packets sent by a client in the network;
selecting, at the device, one or more additional packets sent by the client from which to capture contextual traffic data for the encrypted traffic flow;
capturing, by the device, the contextual traffic data for the encrypted traffic flow from the one or more additional packets sent by the client;
performing, by the device, a classification of the encrypted traffic flow by using the contextual traffic data as input to a machine learning-based classifier; and
generating, by the device, an alert based on the classification of the encrypted traffic flow,
wherein selection of the one or more additional packets sent by the client from which to capture the contextual traffic data is based on the one or more additional packets being: 1) included in a predefined fixed-size set of packets sent sequentially before or after a request packet of the encrypted traffic flow, 2) sent by the client within a predefined timespan of the request packet of the encrypted traffic flow, or 3) associated with a predefined micro-activity performed by the client.
|