| CPC H04L 63/1433 (2013.01) [G06F 3/04847 (2013.01); G06Q 10/06315 (2013.01); G06Q 10/0635 (2013.01); H04L 63/20 (2013.01); G06F 3/04842 (2013.01); G06F 21/577 (2013.01); G06Q 30/018 (2013.01); H04L 41/22 (2013.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01)] | 22 Claims |
|
1. A system, comprising:
a memory configured to store security policies and procedures associated with an enterprise, wherein the security policies and procedures comprise at least one of device information or policy information identifying actions associated with protecting assets of the enterprise and procedure information identifying actions to be performed by personnel to protect the assets of the enterprise;
at least one device comprising at least one processor, wherein the at least one device is configured to:
monitor enterprise activity associated with a plurality of devices associated with the enterprise in accordance with the security policies and procedures stored in the memory,
determine, based on the monitored enterprise activity, whether the enterprise is complying with the security policies and procedures stored in the memory,
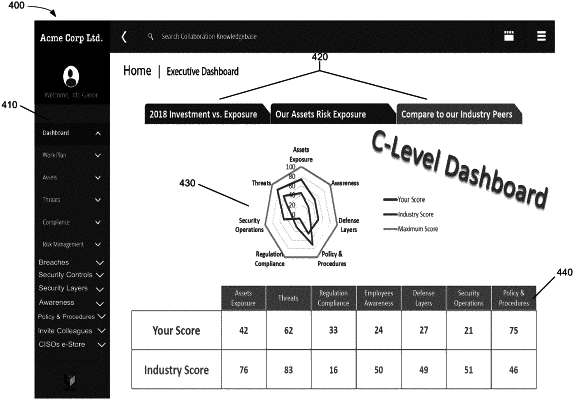
calculate a risk exposure metric for a plurality of the assets of the enterprise based on the monitored enterprise activity and whether the enterprise is complying with the stored security policies and procedures,
output, to a display, information identifying the risk exposure metric associated with at least some of the plurality of the assets, and
generate a plan identifying actions to be taken by the enterprise to reduce the risk exposure metric associated with at least some of the plurality of the assets.
|