| CPC H04L 63/1416 (2013.01) [H04L 61/251 (2013.01); H04L 63/0815 (2013.01); H04L 63/083 (2013.01); H04L 63/0853 (2013.01)] | 20 Claims |
|
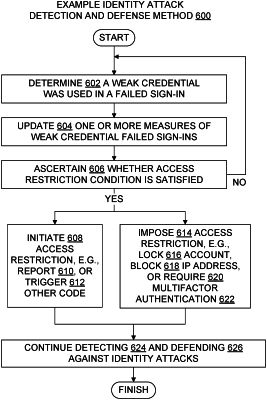
1. An attack detection system which is configured for automatic detection of an identity attack and for initiating an automatic defense against the identity attack, the system comprising:
a digital memory;
a processor in operable communication with the memory, the processor configured to perform steps for detecting an identity attack in or against a monitored network, the steps including (a) determining that a credential used in a failed sign-in to a target account from a source location is a weak credential, (b) in response to the determining, updating a measure of weak credential failed sign-ins, (c) ascertaining that the updated measure satisfies an access restriction condition, and (d) in response to at least the ascertaining, initiating an access restriction on at least one of the target account and the source location, whereby the system enhances cybersecurity by detecting behavior which indicates an identity attack and by initiating an access restriction in response to the behavior, and wherein said detecting is based on at least both noting sign-in failure and determining credential weakness.
|