| CPC G06F 21/577 (2013.01) [G06F 8/71 (2013.01); G06F 21/602 (2013.01); G06N 20/00 (2019.01); H04L 9/0643 (2013.01)] | 20 Claims |
|
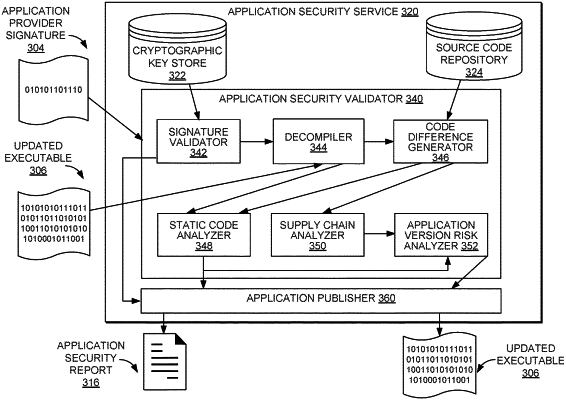
1. A computer-implemented method for identifying suspicious application updates of an application for publishing by a publisher, the method comprising:
identifying at least one difference between updated source code and previous source code without executing and prior to publishing the updated source code, the updated source code corresponding to an updated version of the application that has been updated based at least on a component of the updated source code that is received from an entity separate from the publisher, and the previous source code corresponding to a previous version of the application;
determining a risk score, for the updated version of the application, based on a machine learning (ML) risk model that is employed to analyze the at least one difference between the updated source code and the previous source code, the risk score having a value corresponding to at least one potential security threat that is associated with the updated version of the application and not associated with the previous version of the application; and
based on the risk score being greater than a risk score threshold, providing an indication that the updated version of the application includes a potential security threat.
|