| CPC H04W 12/37 (2021.01) [H04L 63/0876 (2013.01); H04W 8/02 (2013.01); H04W 12/009 (2019.01); H04W 12/66 (2021.01); H04W 12/71 (2021.01)] | 16 Claims |
|
1. A method for suspect device filtering in a wireless communication network, the method comprising:
receiving, at a radio access network, a plurality of requests for a network service from a user device, wherein the user device is associated with a permanent device identifier;
communicating the plurality of requests for the network service to a first network function of a core network, wherein the first network function is associated with the provision of the requested network service;
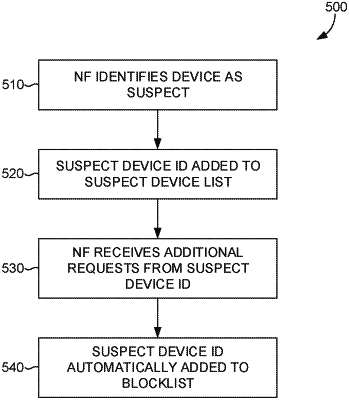
determining, by the first network function, and based at least in part on the receipt of the plurality of requests for the network service from the user device during a first predetermined time period, that the user device is suspect;
based on the determination that the user device is suspect, communicating an indication from the first network function to a second network function of the core network that causes the user device to be added to a first suspect device list maintained on the second network function, the second network function being one or more of a unified data repository and an equipment identity register, wherein the second network function is remote from the first network function;
in response to an acknowledgement from the second network function, associating the user device with a second suspect device list stored locally on the first network function;
receiving, at the radio access network, a subsequent request for the network service from the user device;
communicating the subsequent request for the network service from the radio access network to the first network function; and
determining by the first network function, based on a query of the locally stored second suspect device list, that the user device is blacklisted; and
communicating an access denial for the network service from the first network function to the user device, via the radio access network, without a subsequent query to the second network function,
wherein determining that the user device is suspect comprises the first network function determining that a number of the plurality of requests that have been received by the network function within a predetermined time period exceed a predetermined threshold, and wherein the first network function comprises an access mobility function, and wherein the predetermined threshold and the predetermined time period are modifiably configurable parameters.
|