| CPC H04L 9/3213 (2013.01) [H04L 63/105 (2013.01)] | 20 Claims |
|
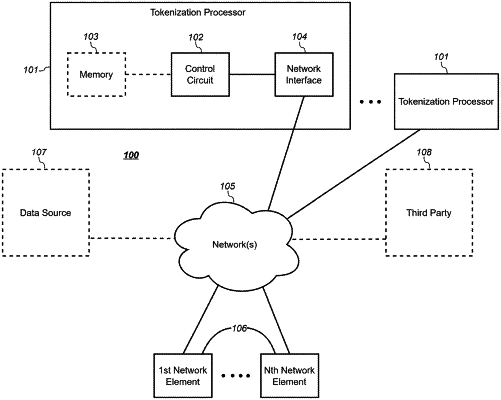
1. A method for tokenization, as a process resulting in at least one reversible token, using a plurality of control circuits wherein each of the control circuits is configured as a tokenization processor that communicates with a requesting network element acting as a requestor, the method comprising:
setting up by a third party of a plurality of tokenization processors, wherein the setting up comprises, at least in part, computation by the third party of an inverse of a first sum of first tokenization processor secrets and randomized splitting of the inverse as a second sum of second tokenization processor secrets, and wherein the first sum and second sum are distinct from one another;
transmitting third tokenization processors secrets comprising at least one of the first tokenization processor secrets and at least one of the second tokenization processor secrets to a first tokenization processor of the plurality of tokenization processors, and transmitting fourth tokenization processor secrets comprising at least one of the first tokenization processor secrets and at least one of the second tokenization processor secrets to a second tokenization processor of the plurality of tokenization processors, wherein the first tokenization processor and the second tokenization processor differ from one another, the third tokenization processor secrets include at least one of the at least one of the first tokenization processor secrets and at least one of the at least one of the second tokenization processor secrets not included within the fourth tokenization processor secrets, and the fourth tokenization processor secrets include at least one of the at least one of the first tokenization processor secrets and at least one of the at least one of the second tokenization processor secrets not included within the third tokenization processor secrets; and
generating by at least the first tokenization processor and the second tokenization processor at least one reversible token, wherein the generating entails use by the first tokenization processor of at least one tokenization processor secret derived from the third tokenization processor secrets and use by the second tokenization processor of at least one tokenization processor secret derived from the fourth tokenization processor secrets, wherein the at least one tokenization processor secret derived from the third tokenization processor secrets and the at least one tokenization processor secret derived from the fourth tokenization processor secret secrets differ from one another.
|