| CPC H04L 9/0894 (2013.01) [H04L 9/008 (2013.01)] | 13 Claims |
|
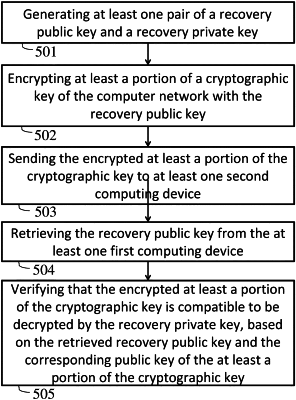
1. A method of verifying that an encrypted cryptographic private key associated with a blockchain based computer network can be decrypted, the method comprising:
encrypting, by at least one first computing device, at least a portion of a cryptographic key of the computer network with a recovery public key, wherein the encryption is carried out using an homomorphically additive encryption scheme;
sending, by the at least one first computing device, the encrypted at least a portion of the cryptographic key to at least one second computing device;
retrieving, by the at least one second computing device, the recovery public key from the at least one first computing device;
verifying, by the at least one second computing device, that the encrypted at least a portion of the cryptographic key is compatible to be decrypted by a recovery private key, based on the retrieved recovery public key and the corresponding public key of the at least a portion of the cryptographic key;
sending, by the at least one first computing device, the recovery private key to a recovery escrow service;
periodically sending, by the at least one first computing device, an arbitrary message to the recovery escrow service, wherein the recovery message is signed by the recovery private key;
publishing the signed arbitrary message in a public repository;
retrieving, by the at least one second computing device, the signed arbitrary message from the public repository;
verifying, by the at least one second computing device, that the encryption of the signed arbitrary message is compatible with the recovery public key; and
verifying, by the at least one second computing device, that the recovery escrow service has the recovery private key.
|