| CPC H04L 63/145 (2013.01) [G06N 5/04 (2013.01); G06N 20/00 (2019.01); H04L 63/105 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01)] | 20 Claims |
|
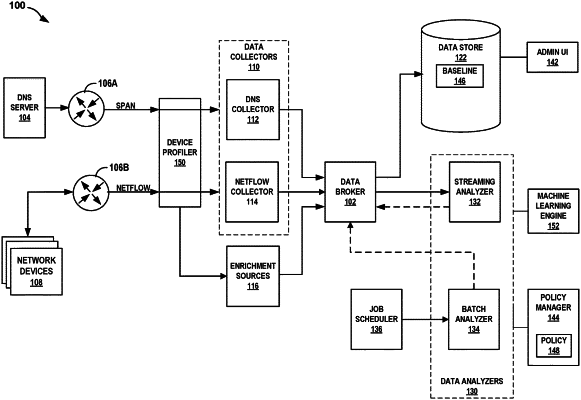
1. A method comprising:
receiving, from a first device on a network, incoming network traffic;
receiving previous network traffic from a second device having the same device type as the first device on an isolated network for a predetermined time period,
creating a network traffic baseline based on the previous network traffic;
comparing the network traffic baseline associated with the incoming network traffic;
determining, based on the comparison, an anomaly type associated with the incoming network traffic; and
changing access to the network by the first device according to an access restriction selected from a set of access restrictions, wherein the access restriction corresponds to the anomaly type.
|