| CPC H04L 63/1433 (2013.01) [G06F 21/577 (2013.01); H04L 45/02 (2013.01); H04L 63/102 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/20 (2013.01)] | 28 Claims |
|
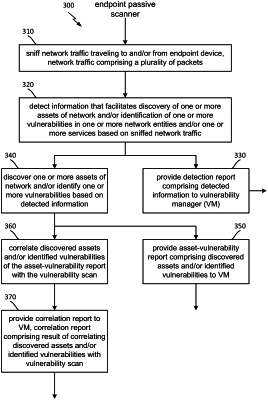
1. A method for passively scanning a network, the method comprising:
sniffing, by an endpoint passive scanner deployed on an endpoint device, network traffic traveling to and/or from the endpoint device, the network traffic comprising a plurality of packets;
detecting, by the endpoint passive scanner, information that facilitates discovery of one or more assets of the network and/or identification of one or more vulnerabilities in one or more network entities and/or one or more services based on the sniffed network traffic; and
performing, by an endpoint agent running on the endpoint device, a vulnerability scan of the endpoint device,
wherein the endpoint passive scanner is deployed as a passive scan library linked to the endpoint agent running on the endpoint device, and
wherein the endpoint passive scanner is configured to run when the endpoint agent calls the passive scan library.
|