| CPC H04L 63/1416 (2013.01) [G06F 9/45558 (2013.01); G06F 21/565 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01); G06F 2221/034 (2013.01)] | 17 Claims |
|
1. A malware analysis method comprising:
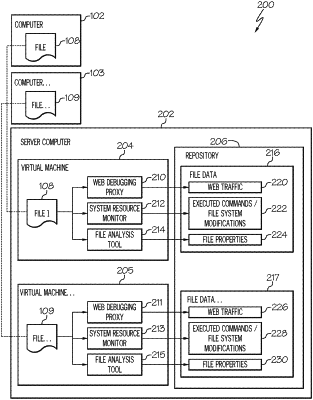
receiving a file on a virtual machine, the virtual machine comprising:
a web debugging proxy, wherein the web debugging proxy is prepared to filter web traffic noise by gathering a baseline reading of web traffic of the virtual machine,
a system resource monitor, and
a file analysis tool;
performing, with the file analysis tool, a static analysis on the file, the static analysis comprising:
determining a set of file properties of the file; and
storing the determined file properties in a repository;
performing, with the web debugging proxy and the system resource monitor, a dynamic analysis on the file, the dynamic analysis comprising:
running the file on the virtual machine;
determining, with the web debugging proxy, web traffic of the virtual machine;
determining, with the system resource monitor, executed commands and modifications to system resources of the virtual machine originating from the file; and
storing the determined traffic and executed commands in the repository.
|