| CPC G06Q 10/0635 (2013.01) [G06F 9/542 (2013.01); G06F 11/079 (2013.01); G06F 16/955 (2019.01); G06F 17/18 (2013.01); G06F 18/214 (2023.01); G06F 18/2178 (2023.01); G06F 18/23213 (2023.01); G06F 18/24143 (2023.01); G06F 21/554 (2013.01); G06F 21/56 (2013.01); G06F 21/562 (2013.01); G06F 21/565 (2013.01); G06N 5/01 (2023.01); G06N 5/022 (2013.01); G06N 5/04 (2013.01); G06N 5/046 (2013.01); G06N 7/00 (2013.01); G06N 20/00 (2019.01); G06N 20/20 (2019.01); G06Q 10/06395 (2013.01); G06V 20/52 (2022.01); H04L 63/0227 (2013.01); H04L 63/0263 (2013.01); H04L 63/1408 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); H04L 63/20 (2013.01); G06Q 30/0185 (2013.01); G06Q 30/0283 (2013.01)] | 20 Claims |
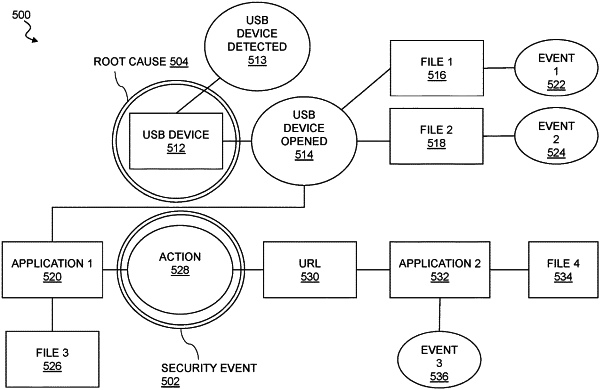
|
7. A method comprising:
providing a valuation model for automatically estimating a business value of a file, wherein providing the valuation model includes creating a model to estimate the business value based on a training set of files each having a known business value, wherein the business value is based on at least one of a file location and an access control list;
analyzing a plurality of files within an enterprise network for a threat level using an integrative model based on one or more of behavioral tags, executable file paths, and Uniform Resource Locators;
identifying one or more intermediate threats associated with the plurality of files that are not within a predetermined confidence level of safe or malicious according to the integrative model;
determining an estimated business value for each of the one or more intermediate threats using the valuation model;
ranking the one or more intermediate threats for presentation within a user interface based on a combination of a likelihood of maliciousness determined according to the integrative model and the estimated business value determined according to the valuation model; and
presenting the one or more intermediate threats to a user in the user interface for human evaluation.
|