| CPC G06N 5/022 (2013.01) [G06N 5/01 (2023.01)] | 20 Claims |
|
1. A system for generating an attack event log comprising:
a storage device for storing an event log template;
a processor to:
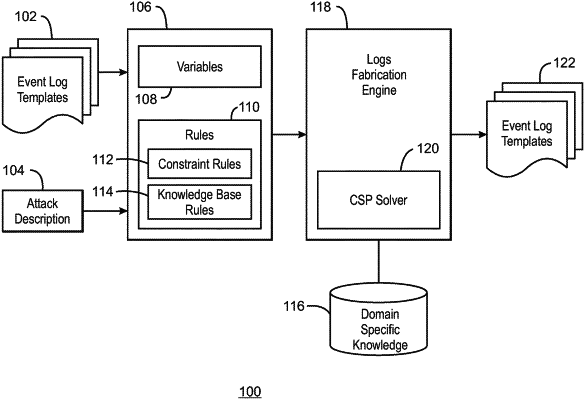
receive a selection of event log templates representing different log sources and entry types, wherein log entries in the event log templates do not represent a consistent attack scenario;
receive an attack description comprising user instructions to fabricate synthetic log entries according to a format defined in the event log templates, the attack description comprising variables and rules for determining values for the variables;
automatically generate the attack event log representing an attack scenario and comprising a synthetic log entry that is fabricated by determining a value that satisfies the rules and writing the value into selected fields of the event log templates and combining the resulting log entries representing a plurality of different types of sub attacks using a temporal ordering of events in a manner that is consistent across the attack scenario;
integrate a benign event log file that excludes attacks with the automatically generated attack event log to generate a stream of events that is consistent based on the automatically generated attack event log; and
send the generated stream of events to a Security Information and Event Management (SIEM) system, wherein the generated stream of events is used to test the SIEM.
|