| CPC G06F 21/84 (2013.01) [G06F 21/31 (2013.01); G06F 21/577 (2013.01); G06F 21/602 (2013.01); G06F 2221/2103 (2013.01)] | 17 Claims |
|
1. A computer-implemented method, comprising:
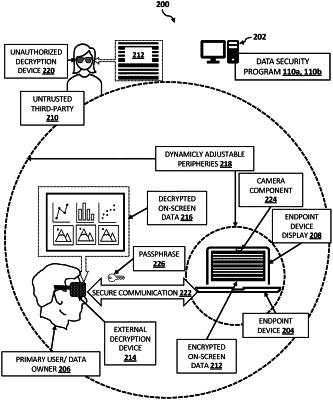
encrypting an on-screen data for viewing by a primary user, wherein the encrypted on-screen data is rendered on a display of an endpoint device of the primary user based on a security policy set by the primary user;
identifying a second external decryption device within a periphery defined by the endpoint device based on the security policy set by the primary user, wherein the identified second external decryption device is associated with a secondary user;
transmitting a challenge to the identified second external decryption device including a request for a passphrase generated by the primary user of the endpoint device; and
authenticating the identified second external decryption device based on receiving a response from the identified second external decryption device including the passphrase generated by the primary user of the endpoint device; and
decrypting the encrypted on-screen data for viewing by the secondary user using the authenticated identified second external decryption device.
|