| CPC G06F 21/6227 (2013.01) [G06F 16/9024 (2019.01); G06N 3/088 (2013.01)] | 17 Claims |
|
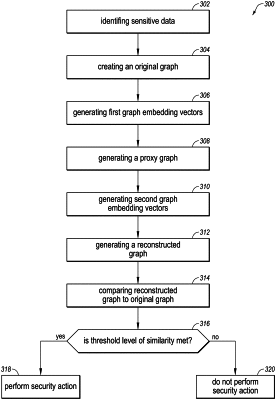
1. A computer-implemented method for protecting sensitive data from being exposed in graph embedding vectors, at least a portion of the method being performed by a computing device comprising one or more processors, the computer-implemented method comprising:
identifying sensitive data;
creating an original graph from the sensitive data, the original graph including a plurality of original nodes and original edges connecting the original nodes;
generating first graph embedding vectors from the original graph, the first graph embedding vectors including one or more attributes of the original nodes;
generating from the first graph embedding vectors a proxy graph, the proxy graph including a plurality of proxy nodes and proxy edges connecting the proxy nodes, the proxy nodes including the one or more attributes of the original nodes included in the first graph embedding vectors;
generating second graph embedding vectors by encoding the proxy graph;
generating a reconstructed graph by decoding the second graph embedding vectors;
comparing the reconstructed graph to the original graph to determine whether a threshold level of similarity is met; and
in response to determining that the threshold level of similarity is met, performing a security action to protect the sensitive data from being exposed to a third-party through the first graph embedding vectors.
|