| CPC G06F 21/575 (2013.01) [G06F 11/1435 (2013.01); G06F 11/1464 (2013.01); G06F 21/572 (2013.01); G06F 21/78 (2013.01); H04L 9/0897 (2013.01); G06F 9/4401 (2013.01); G06F 2201/84 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
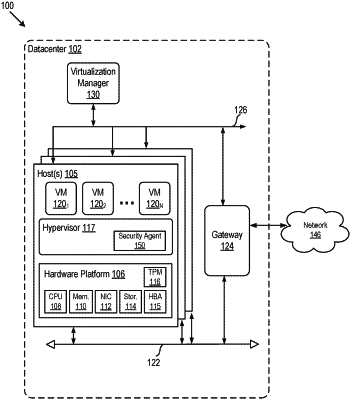
16. A computer system, comprising:
a memory; and
a processor coupled to the memory, the processor being configured to:
identify a portion of an OS disk of a host computing device, the portion of the OS disk including one or more files that store configuration data associated with OS binaries executed on the host computing device;
encrypt, using an encryption key, only the portion of the OS disk;
seal the encryption key to a trusted platform module (TPM) of the host computing device; and
boot the host computing device comprising:
attempting to unseal the encryption key by authenticating one or more of the OS binaries with the TPM;
when authenticating the one or more of the OS binaries is successful, completing boot of the host computing device by decrypting the portion of the OS disk using the encryption key to obtain the configuration data; and
when authenticating the one or more of the OS binaries is not successful, aborting boot of the host computing device.
|