| CPC B60R 25/1025 (2013.01) [B60R 25/245 (2013.01); G07C 9/00309 (2013.01); H04B 17/318 (2015.01); H04L 9/50 (2022.05); G07C 2009/00412 (2013.01); G07C 2009/00555 (2013.01); G07C 2009/00769 (2013.01); G07C 2209/08 (2013.01); G07C 2209/64 (2013.01); H04L 2209/84 (2013.01)] | 20 Claims |
|
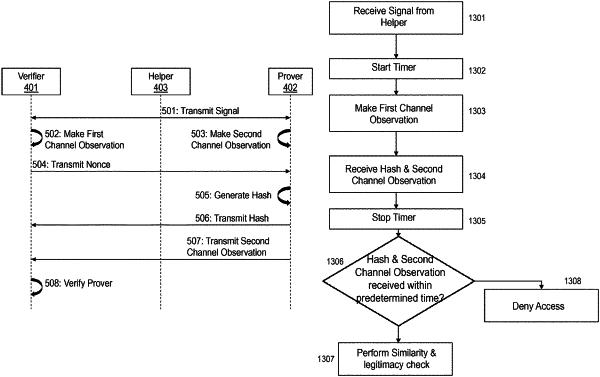
12. A system for controlling access to a resource, the system comprising a first component, a second component and a third component, wherein:
the first component comprises a first cryptographic key;
the second component comprises a second cryptographic key; and
wherein:
the third component is configured to:
transmit a signal;
the second component is configured to:
generate a second channel observation;
generate a first data value based on the second channel observation and the second cryptographic key; and
transmit to the first component, the second channel observation and the first data value; and
the first component is configured to:
generate a first channel observation;
verify the second component based on the second channel observation, the first cryptographic key and the first data value; and
allow access to the resource in response to determining that the second component is: 1) permitted to gain access to the resource; and 2) located proximate to the first component.
|