| CPC H04W 12/065 (2021.01) [H04W 4/14 (2013.01); H04W 12/61 (2021.01); H04W 12/69 (2021.01)] | 8 Claims |
|
1. A method for authenticating users of mobile communication devices through mobility traces, comprising the following steps:
recording one or more interactions of a user with at least one network element through a mobile device of the user subscribed in a network service provider;
wherein further comprising the following steps:
recording, by the at least one network element, a timestamp (T), associated with the recorded interactions, a unique identifier of the mobile device, a unique identifier of the user and a unique identifier of the network element;
by using all the data recorded in the previous steps, computing a network interaction track, NIT, by the network service provider;
by using the computed NIT, obtaining at the network service provider an authentication result indicating either a success or a failure of the user authentication;
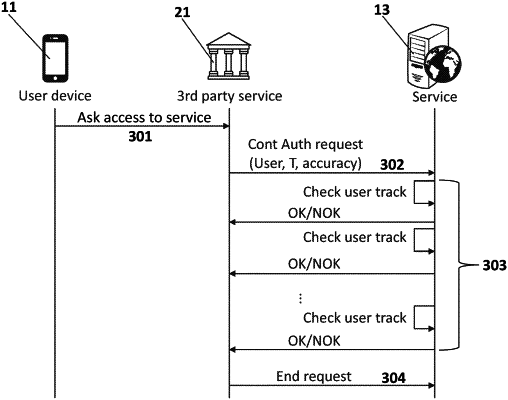
sending an authentication status check request to the network service provider from a third-party service provider to which the user is asking access through the mobile device, the authentication status check request comprising the user identifier and the timestamp (T) for which the authentication status is requested to be checked, and sending the authentication result from the network service provider to the third-party service provider,
wherein the authentication status check request further comprises a user authentication request mode selected from single authentication and continuous authentication and, if the user authentication request mode selected is continuous authentication, the authentication status check request further comprises an authentication time period, and
wherein the authentication result is obtained by the network service provider and sent to the third-party service provider periodically for every authentication time period until an end of the user authentication request is received from the third-party service provider at the network service provider;
and wherein computing the NIT by the network service provider comprises generating a regular NIT at a time instant t=T, being T the timestamp, and generating at least one temporary NIT at a next time t′=T+M, being M the authentication time period, and wherein obtaining the authentication result by the network service provider comprises comparing the at least one temporary NIT with the regular NIT generated for the same user to detect anomalies.
|