| CPC H04L 63/20 (2013.01) [G06F 21/52 (2013.01); G06F 21/554 (2013.01); G06N 5/01 (2023.01); H04L 63/168 (2013.01); H04L 67/133 (2022.05); G06F 2221/033 (2013.01)] | 17 Claims |
|
1. A computer implemented method for dynamically enforcing, at runtime, a multi-API security policy that covers multiple API calls of a multi-API transaction, the method comprising:
reading logs of calls to multiple APIs of a multi-API transaction, the multi-API call transaction comprising a call to an initial API, and calls made to subsequent APIs by the initial API and by other subsequent APIs;
identifying, from the logs, data objects used by the multiple APIs;
assigning specific data labels to specific fields of data objects used by the multiple APIs, the specific data labels providing consistent identification of data fields of specific types across the multiple APIs;
identifying linkages between specific ones of the multiple APIs, based on the consistent identification of data fields of specific types across the multiple APIs;
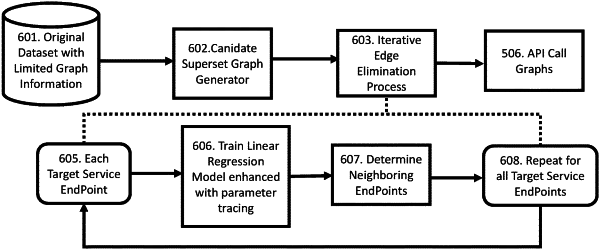
grouping limited information available concerning the multiple APIs and relationships between them in a candidate superset graph;
growing the candidate superset graph by an iterative edge elimination process to construct an API call graph identifying a sequence of API calls made during the multi-API transaction, wherein a linear regression model is used to determine neighbors of service endpoints; and
using the API call graph identifying the sequence of API calls to enforce the multi-API security policy that covers multiple API calls of the multi-API transaction, the multi-API security policy using the specific data labels to consistently identify data fields of specific types across the multiple APIs.
|