| CPC G06F 3/0623 (2013.01) [G06F 3/067 (2013.01); G06F 3/0607 (2013.01); G06F 12/1408 (2013.01); G06F 12/1458 (2013.01); G06F 16/258 (2019.01); G06F 16/907 (2019.01); G06F 2212/1052 (2013.01); G06F 2212/402 (2013.01)] | 18 Claims |
|
1. A method of performing a security action on electronic data residing on an electronic data storage system to prevent subsequent unauthorized access comprising:
maintaining an external metadata management system remote, separate, and independent from and in communication with a plurality of electronic data storage systems, wherein each electronic data storage system stores electronic data and comprises one or more processors having circuitry and logic for performing calculations and logic operations and wherein the external metadata management system comprises one or more metadata processors having circuitry and logic for performing calculations and logic operations;
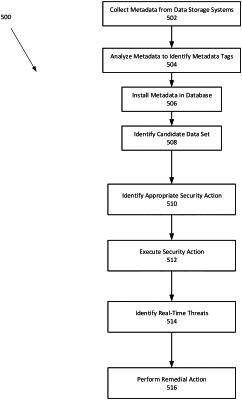
operating the external metadata management system by the one or more metadata processors, wherein operating the external metadata management system comprises storing metadata on the external metadata management system that corresponds to the electronic data residing on the plurality of data storage systems;
identifying, by the external metadata management system using information included in the external metadata management system, a candidate data set residing on at least one of the plurality of data storage systems on which at least one security action should be performed, wherein the at least one of the plurality of data storage systems is remote, separate and independent from the external metadata management system and the at least one security action comprises at least one of a group consisting of: encryption; redaction; application of access controls; application of dissemination controls; inclusion and/or exclusion of partitions, folders, files, file extensions or other divisions of information; specifying encryption protocols and/or levels for encryption; applying and/or configuring operating system protection rules; applying and/or configuring user authentication mechanisms; applying and/or configuring device usage controls; auditing of system and/or user behavior; applying and/or configuring firewall rules; applying and/or configuring rules regarding anti-virus, anti-spam, and/or anti-spyware; applying and/or configuring rules regarding provisioning, management, and/or integration of third-party applications; and combinations thereof;
in response to identifying the candidate data set residing on the at least one of the plurality of data storage systems on which at least one security action should be performed, identifying by the external metadata management system the at least one security action that should be performed on the identified candidate data set; and
implementing, in response to identifying the at least one security action, the at least one identified security action on the identified candidate data set residing on the at least one of the plurality of data storage systems to prevent subsequent unauthorized access to the identified candidate data set residing on the at least one of the plurality of data storage systems.
|