| CPC G06F 21/6218 (2013.01) [G06F 11/1458 (2013.01); H04L 63/105 (2013.01); G06F 2201/84 (2013.01)] | 20 Claims |
|
1. A computer-implemented method, comprising:
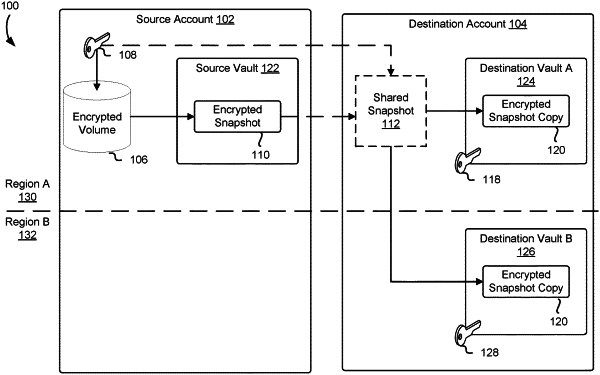
obtaining source account attributes for a backup operation from a source account to a destination account, wherein the backup operation causes data to be copied from the source account to the destination account based at least in part on the source account attributes, wherein the source account is associated with a first member of an organization and the destination account is associated with a second member of the organization;
generating a first determination that cross-account backup operations from the source account to the destination account are allowed based at least in part on a first security policy associated with the organization;
obtaining information from a second security policy associated with a portion of the destination account, the information identifying a logical storage location associated with the destination account for maintaining the data;
generating a second determination that the source account and the destination account are members of the organization;
authenticating the source account and the destination account to determine that the backup operation can be performed from the source account to the destination account; and
performing the backup operation as a result of the first determination indicating that permissions associated with the source account are insufficient to delete the data and the second determination indicating that the permissions associated with the destination account are sufficient to receive the data from the source account, wherein the backup operation includes storing a copy of an encrypted version of the data in the logical storage location as a result of exposing, to the destination account, the encrypted version and a corresponding key.
|