| CPC H04W 12/122 (2021.01) [H04W 12/106 (2021.01); H04W 28/0268 (2013.01)] | 13 Claims |
|
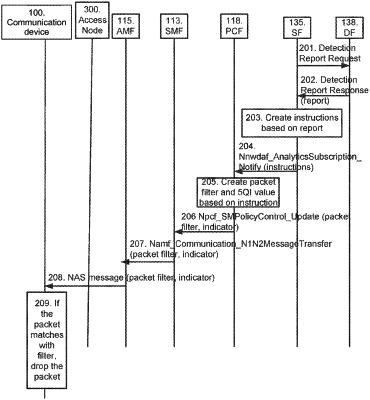
1. A method performed by a core network node for enabling handling of data packets in a wireless communication system, the core network node being comprised in a core network of the wireless communication system, the method comprising:
identifying a potentially malicious service data flow associated with a communication device served by an access network of the wireless communication system;
assigning, to the potentially malicious service data flow, an identifier value to an identifier, wherein the identifier value indicates that data packets associated with the potentially malicious service data flow is to be handled according to a packet handling rule for potentially malicious data packets; and
providing an identifier comprising the identifier value towards the communication device towards at least one of:
an access node that serves the communication device in the access n, and
a second core network node that processes data packets to and from the communication device,
wherein the identifier value indicates at least one of:
that data packets associated with the potentially malicious service data flow is to be dropped by at least one of the communication device and the access node;
that data packets associated with the potentially malicious service data flow is to be monitored within the access network;
that the communication device associated with the potentially malicious service data flow is to be deprioritized by the access node;
that network resources for the communication device associated with the potentially malicious service data flow is to be restricted by the access node; and
wherein the identifier value implicitly indicates that data packets belonging to the potentially malicious service data flow is to be dropped or monitored.
|