| CPC H04L 63/20 (2013.01) [H04L 63/101 (2013.01); H04L 63/145 (2013.01); H04L 63/1416 (2013.01)] | 18 Claims |
|
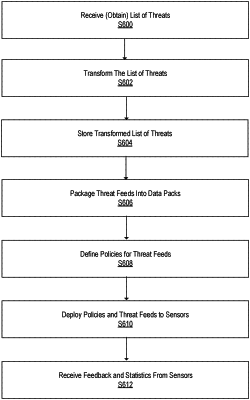
1. A method comprising:
receiving a list of network threats;
transforming the list of network threats into a format compatible with existing exchange protocols between a server and sensors of a network;
packaging the transformed list into existing data packs exchanged between the server and the sensors;
defining policies for the threats by creating annotations to tag compromised network elements;
deploying the defined policies and the existing data packs with the transformed list of threats feeds to the sensors;
collecting continuous feedback from the sensors on various statistics collected by the sensors on performance and data traffic between their respective network elements; and
updating the policies based upon the collected statistics.
|