| CPC H04L 63/1483 (2013.01) [H04L 51/212 (2022.05); H04L 63/12 (2013.01); H04L 63/123 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 9/0643 (2013.01); H04L 9/0894 (2013.01); H04L 9/3239 (2013.01)] | 18 Claims |
|
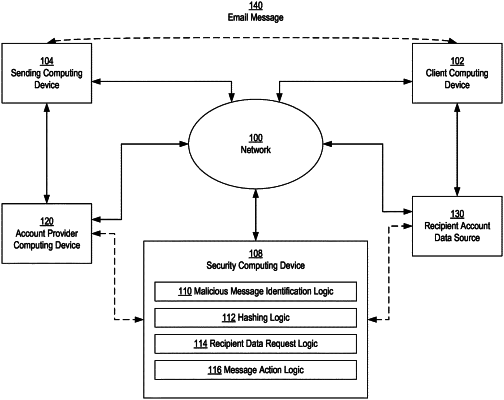
1. A computer-implemented method executed by one or more email detection computers, the method comprising:
receiving, from a digital electronic computer network, a first email message that is directed to a first recipient account from a first sender account, the first email message being associated with a plurality of attributes;
determining that the first email message is a phishing email;
extracting, from the first email message, a subset of the plurality of attributes, the subset of the plurality of attributes comprising a plurality of fixed attributes and a plurality of transformable attributes, the plurality of fixed attributes of the first email message being two or more of a thread count; an attachment count; a TO recipient count; a CC recipient count; a number of URLs within a body of the first email message; a number of links within the body of the first email message; or a BCC recipient count;
transforming each particular transformable attribute of the plurality of transformable attributes to a normalized representation of that particular transformable attribute;
concatenating the plurality of fixed attributes and the normalized representations of the plurality of transformable attributes into a string representation;
generating a hash representation of the subset of the plurality of attributes based on the string representation of the concatenated plurality of fixed attributes and the normalized representations of the plurality of transformable attributes;
storing the hash representation of the subset of the plurality of attributes of the first email message in a database;
receiving, from the digital electronic computer network, a second email message that is directed to a second recipient account from a second sender account;
determining that the second email message is a phishing email based on the hash representation corresponding to the first email message.
|