| CPC H04L 63/145 (2013.01) [G06F 21/52 (2013.01); G06F 21/56 (2013.01); G06F 2221/033 (2013.01); G06F 2221/2143 (2013.01)] | 18 Claims |
|
1. A system for suspending a computing device suspected of being infected by a malicious code, comprising:
a memory operable to store a software instruction that is executed to initiate a suspension procedure, wherein:
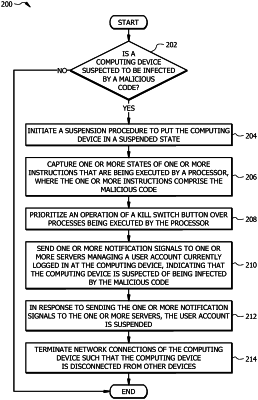
the suspension procedure is initiated when a computing device is suspected of being infected by a malicious code, and
when the malicious code is executed, the computing device becomes vulnerable to security threats comprising an unauthorized access to the memory;
a processor, operably coupled with the memory, configured to:
receive, from a user, a triggering signal to initiate the suspension procedure;
capture one or more states of one or more instructions that are being executed by the processor, wherein the one or more instructions comprise the malicious code;
store the captured one or more states in the memory;
suppress the one or more instructions comprising the malicious code;
send one or more notification signals to one or more servers managing a user account associated with the user currently logged in at the computing device, indicating that the computing device is suspected of having been infected by the malicious code;
in response to sending the one or more notification signals to the one or more servers, the user account is suspended;
terminate network connections of the computing device such that the computing device is disconnected from other devices;
erase a particular portion of the memory in which boot up instructions are stored without which the computing device cannot be restarted, wherein the particular portion includes an address to a boot cycle operation;
determine a source of the malicious code from the stored captured one or more states in the memory; and
initiate security threat investigations using the determined source of the malicious code.
|