| CPC H04L 63/1425 (2013.01) [H04L 63/105 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); H04L 63/168 (2013.01); H04L 67/535 (2022.05)] | 19 Claims |
|
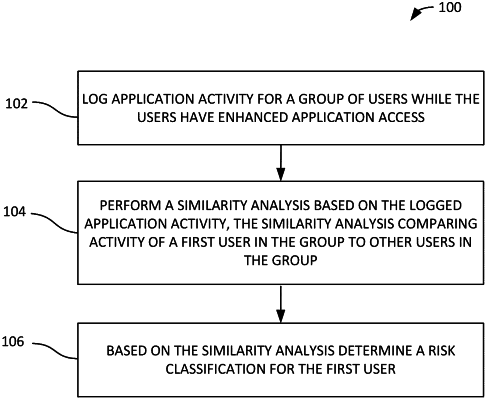
1. A method, comprising:
logging application activity for a group of users while the users have enhanced access to one or more applications;
receiving a request for an enhanced access session for a first user in the group, wherein enhanced access comprises temporarily granting expanded permissions, access to additional functionality, or access to additional data;
performing a similarity analysis based on the logged application activity, the similarity analysis comparing application activity of the first user in the group and application activity of other users in the group;
based on the similarity analysis, determining a risk classification for the first user; and
based on the risk classification, granting or denying the request for the enhanced access session for the first user in the group.
|